It seems that the current trend on social media is overwhelmingly conspiracy theories, especially as elections draw near. I’m not particularly drawn to the political ones, but I’m gripped by a conspiracy theory regarding encryption that’s threatening to upend my world.
 Venn, embodying the curiosity of her engineering owner and her own role as a playful puppy, adores dismantling her toys to uncover what lies inside. Unfortunately, her knack for engineering doesn’t stretch to reassembling them. Hence, we’ve had to ration two toys, give or take one, daily for her explorative demolition. It took some explaining to differentiate between a ‘quota’ and an ‘allocation’ to her. Before that revelation, she was earnestly striving to surpass her daily limit, as if it were a challenge.
Venn, embodying the curiosity of her engineering owner and her own role as a playful puppy, adores dismantling her toys to uncover what lies inside. Unfortunately, her knack for engineering doesn’t stretch to reassembling them. Hence, we’ve had to ration two toys, give or take one, daily for her explorative demolition. It took some explaining to differentiate between a ‘quota’ and an ‘allocation’ to her. Before that revelation, she was earnestly striving to surpass her daily limit, as if it were a challenge.
This nuance matters deeply to me because I’ve set my own limit for engaging with political and conspiracy theory posts at a sparse two per year. If it were a quota, the current shenanigans of our Congress and Supreme Court could easily become the sole focus of my writings.
Today’s dive into conspiracy theories centers around our government and the enigma of encryption. Encryption is paradoxical, a battlefield of ideals. We all crave robust encryption to shield our bank accounts from malevolent eyes. Yet, governments yearn for keys to unlock any message potentially harboring sinister plans. From the government’s perspective, the solution appears straightforward: a backdoor for their eyes only, guarded by promises to keep this access out of the public realm. The tales of disgruntled government workers leveraging such access for personal gain or vendetta? Pure fiction, or so they assert. As ludicrous as a Supreme Court Justice oblivious to the gift restrictions binding every other government worker — as if they stand above.
The adage that if you’ve done nothing wrong, you have nothing to fear, rings hollow. No matter the security clearances or the roles, people will be people — prone to vengeance, greed, or mere incompetence. Look closely at our Congress members. How many of them would you trust with unfettered access to the minutiae of your life? Remember, it only takes one corrupted soul to throw your existence into chaos, innocence notwithstanding.
Apple’s inability to decrypt iPhones anymore is telling. The demands from every level of government became so overwhelming they had to establish a whole division just to cope. The idea that a secret key could remain secret is fanciful at best.
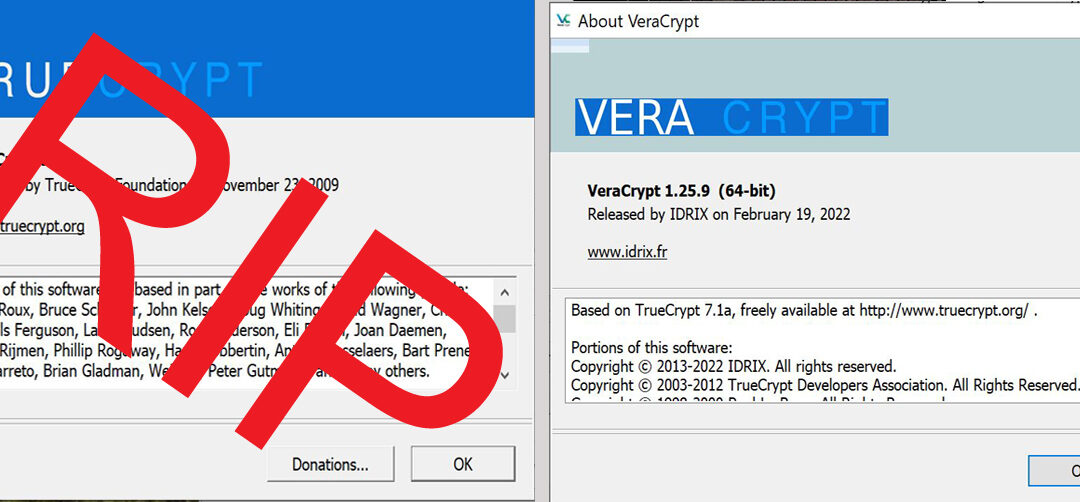
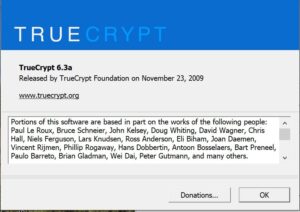 Now, for the conspiracy theory I promised. My archives are safeguarded with TrueCrypt 6.3A, a relic from November of 2009. There’s a newer version, but it was intentionally crippled to direct users towards Microsoft BitLocker. Long prior to the final version, I chose TrueCrypt because it empowered me with a security phrase — lose it, and my records vanish forever. It even allowed the creation of a hidden encrypted container within another, known only to me. This feature was golden in an era when US Officials boldly claimed the right to demand your passwords. I’ve never used that feature, never felt the need, but the very fact that such a comprehensive level of encryption was considered speaks volumes.
Now, for the conspiracy theory I promised. My archives are safeguarded with TrueCrypt 6.3A, a relic from November of 2009. There’s a newer version, but it was intentionally crippled to direct users towards Microsoft BitLocker. Long prior to the final version, I chose TrueCrypt because it empowered me with a security phrase — lose it, and my records vanish forever. It even allowed the creation of a hidden encrypted container within another, known only to me. This feature was golden in an era when US Officials boldly claimed the right to demand your passwords. I’ve never used that feature, never felt the need, but the very fact that such a comprehensive level of encryption was considered speaks volumes.
The official line is that TrueCrypt’s development ceased because BitLocker simply did it better. This feels as believable as Ford shutting down because GM supposedly makes superior cars, then rigging their vehicles to malfunction and dial GM dealerships for help. Implausible.
Despite TrueCrypt not being open source and pending a thorough security audit, when the audit finally came, it revealed no significant vulnerabilities. Yes, there were minor issues, but on the whole, it stood more secure than BitLocker at the time.
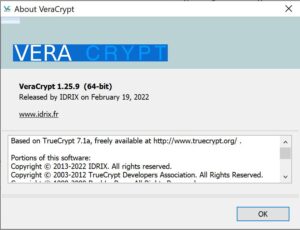 Enter VeraCrypt, a French programming team’s answer to TrueCrypt’s legacy. They addressed many of the audit’s concerns while preserving compatibility with TrueCrypt containers and continuing to offer the program for free, including the hidden containers feature.
Enter VeraCrypt, a French programming team’s answer to TrueCrypt’s legacy. They addressed many of the audit’s concerns while preserving compatibility with TrueCrypt containers and continuing to offer the program for free, including the hidden containers feature.
Designed in the time of Windows XP, as Windows evolves, my version of TrueCrypt is gradually losing its compatibility. VeraCrypt remains supported, but they’ve finally abandoned backward compatibility with TrueCrypt in order to meet modern security standards and ensure alignment with Microsoft.
The signs are clear. Eventually, a Microsoft update will render TrueCrypt inoperable, leaving me with encrypted records I can no longer access. With governments increasingly legislating backdoors into encryption products, the dilemma deepens. Do I place my trust in VeraCrypt, bidding a heartfelt farewell to TrueCrypt? Or do I venture into the unknown, potentially complicit with covert government agreements? And what exactly are France’s laws on encryption?
The thought that my new encryption solution might be clandestinely crafted by the NSA doesn’t seem far-fetched. The more I age, the more I perceive governments as a mix of a few dedicated servants, many ordinary individuals striving only to survive, and a sprinkling of corrupt figures lured by the siren call of power. These are the people I have to trust if I embrace modern encryption applications? Welcome to the digital age, where your privacy is legislated by people still struggling to understand the difference between SMS and POP3.
© 2024, Byron Seastrunk. All rights reserved.