When it comes to computer security, I used to pride myself on being pretty savvy. That self-assuredness shattered when I had the daunting task of replacing my wife’s computer. The moment revealed to me a shocking truth about my own security ignorance.
Her ancient machine wasn’t quite dead, but it was gasping for life. I had already been forced to replace the motherboard battery because it was forgetting all its settings between startups. That only bought me a month of peace. Now it was displaying overtemp warnings immediately on start-up.
My wife is no longer a dedicated gamer, having found a far less judgmental crowd in the canine Agility community. This shift to a more physically active hobby, allowed me to embrace my inner penny-pincher and opt for a refurbished computer from Amazon. Sure, it’s a gamble, slightly riskier than buying brand new, and you’re not exactly getting the cream of the tech crop. Yet, the allure of saving money was irresistible, and Amazon’s warranty offered a safety net that was hard to ignore.

My workshop computer
Nor was this my first refurbished computer. With the laser engraver and CNC, I was already using one in in my workshop. Thanks to this one, I knew the solid-state drives used in these computers are as cheap as they come. Likewise, my wife’s photography hobby required a lot of storage. I would replace her drive immediately with a two-terabyte drive identical to the one already in use by my wife.
When I embark on building up a new computer, I always use a new drive and never, ever, touch the old drive. This philosophy has save me countless times. For this transfer, I chose to use EaseUS Todo PCTrans. It offered to transfer both programs and data seamlessly. Of course, “seamlessly” meant I still had to buy a number of new software licenses.
I bear the blame for the chaos that ensued. That and a short window of time while my wife was at a dog show. Reading the PCTrans instructions a little closer might have avoided a lot of frustration. In my attempt to transfer data, I accidentally created two incomplete user profiles on the new drive. Trying to salvage the situation, I merged one profile into the other, resulting in lost passwords and cookies. The issue came to a head when, days later, my wife noticed several passwords were missing from her browser.
We use KeePass as a password manager. It’s free, available for a number of platforms and the database is portable. Despite our reliance on the password manager, the ease with which browsers suggest saving passwords had lulled us into a false sense of security and we did occasionally use the browser to store passwords. Confronted with the missing passwords dilemma, I could hardly lecture her when I was guilty of the same oversight.
In a bid to recover the lost passwords, I turned to her old computer (once again my philosophy pays off), fully expecting to need Wireshark to extract passwords. The solution, however, was embarrassingly simple, so much so that I vowed never to trust a browser with my passwords again.
This isn’t a tutorial for every browser variant out there, but the process is startlingly similar across the board. Whether it’s Chrome, a Chrome offshoot like Vivaldi (my browser choice), or Firefox, navigating to the security and passwords section of the settings laid bare a shocking revelation: all her passwords, stored in PLAIN TEXT for anyone with access to see. The ease with which I retrieved every lost password—and then some—was a wake-up call.
I’ve also tried this on Edge (must be signed into your Microsoft account) and Safari. Safari actually asked me for the computer password. I suspect that like Edge, you have be signed into your Google account to see your Chrome passwords but Google has made it incredibly difficult to sign out of your account.

A bad day in the making!
Is this easy access to your passwords a genuine security risk? It might not seem so at first, considering someone would need access to your device. But then, how many of us diligently lock our computers every time we step away? And who among us hasn’t left their device unguarded, however briefly? The thought alone is enough to send shivers down your spine.
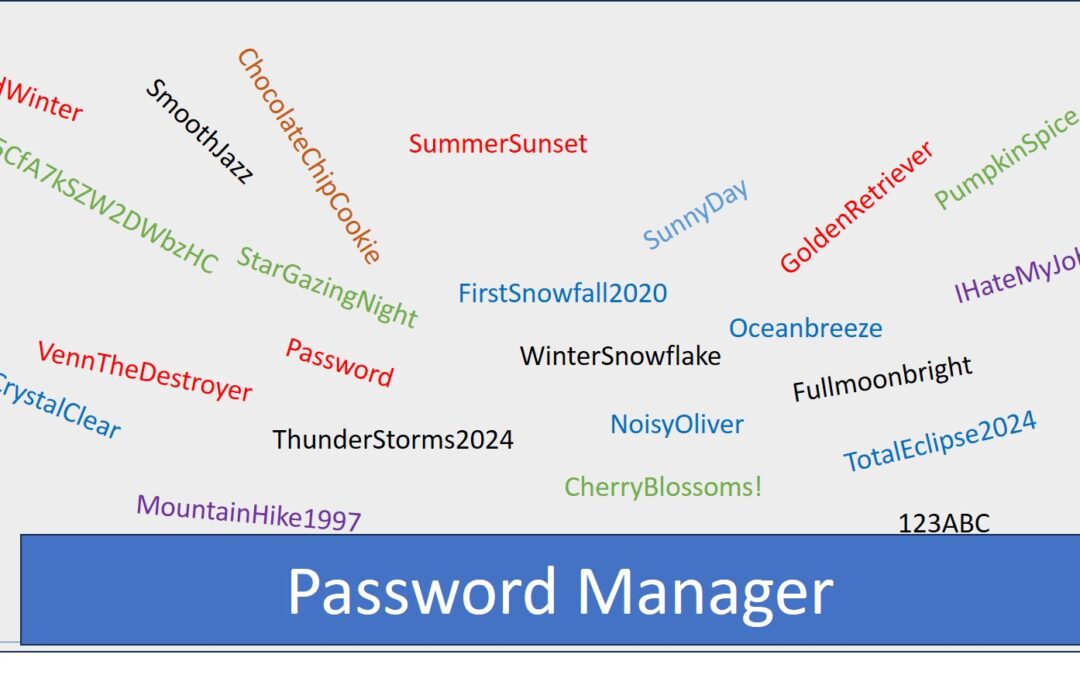
More alarming still is the potential for someone to gain complete insight into your digital life if your passwords are predictable or themed. This realization struck a chord with me, highlighting a glaring vulnerability in what I had believed was a reasonably secure system. If you’re anything like me, this might be a sobering moment, but not necessarily a cause for panic, provided you’ve taken basic security measures, two factor authentication, never storing credit card data with a site and strong passwords. For those with a more lax approach to computer security, however, this could be a harrowing wake-up call.
Consequently, we’ve drastically reduced our reliance on browsers for password storage, making an exception only for inconsequential sites. For everything else, we’ve used our password manager, creating complex, hacker-proof passwords. This incident was a humble reminder of the constant vigilance required in safeguarding our digital lives, underscoring that security is not just about the measures in place, but also about our everyday practices and awareness.
© 2024, Byron Seastrunk. All rights reserved.










Recent Comments